Labels: Spam
Archive
- ► 2010 (6778)
- ► 2009 (533)
Anti-Spam Technologies Tweet
Tuesday, December 23, 2008
Labels: Spam
Posted by
openews
at
5:21 AM
0
comments
![]()
Spamming and Dark Traffic Tweet
Labels: Spam , Web Traffic
Posted by
openews
at
5:07 AM
0
comments
![]()
PageRank Vs Alexa Tweet
Tuesday, December 16, 2008
PageRank related with many numbers link your site to other link, where the page always appear on the top search engines and needed the right keywords with relevant contents. PageRank not real traffic like Alexa ranking but PageRank only algorithm how important the page for everyone.
Alexa ranking is real traffic, where to improve alexa ranking can use other services that provide traffic, such as directory website, buy traffic on google adwords or others service. Higher Alexa traffic does not a website the index by google. So, PageRank and Alexa both very important as indicator the website needed lot of user anytime, anywhere and get it as soon as possible. Good luck.
More about PageRank : Wikipedia
Labels: Web Traffic
Posted by
openews
at
12:08 PM
0
comments
![]()
Choose a Laptop Computer Tweet
Tuesday, December 9, 2008
 Computers are a tool that is very important for those who use a computer every day as tools to complete the work done, such as data processing. With the progress of technology, this form of a computer when a smaller, more lightweight (laptop) and can taken you like.
Computers are a tool that is very important for those who use a computer every day as tools to complete the work done, such as data processing. With the progress of technology, this form of a computer when a smaller, more lightweight (laptop) and can taken you like.This laptop easy to use and can run many applications such as Like desktop computer. Applications that can run the video, spreedsheet, music, VoIP and so forth. Computer technology is a very rapid development. Many products are offered with prices that vary.
Consideration depending on the price of some of the existing specifications such as processor, big hard drives, RAM, and a computer model, VGA and so forth. To choose a laptop computer you should note the specifications are offered, whether in accordance with the application that you will use.
In choosing a laptop computer also needs to be: Is the laptop computer can be upgraded in the day to improve the performance and the size of the cache memory that serves to accelerate the process of read / write. Before you buy a laptop computer you should find plenty of information so that one does not choose when to buy your dream laptop.
Labels: Laptop
Posted by
openews
at
9:38 PM
0
comments
![]()
Check IP Address Tweet
Friday, December 5, 2008
Data shown on this gadget is the IP address of the data that you connect with the Internet network and you can also check the IP address of other locations around the world.
If you use a home router to connect to the Internet is usually the IP address will be shown is the address of the router or your proxy and your IP address (the IP public) will always change every login to the network or get a new IP address each session.
Labels: Internet
Posted by
openews
at
7:56 AM
0
comments
![]()
Definitions Of Programmable Logic Controller (PLC) Tweet
Saturday, November 22, 2008
 Programmable Logic Controllers (PLC) is a computer that is easy to use electronic or user-friendly control functions that have for various types and levels of difficulty diverse. Definition Programmable Logic Controller is electronic systems that operate digital and designed for use in the environmental industry, which uses a memory system that can be programmed for storage in the internal instructions that implement specific functions such as logic, sequence, time, counter and operating aritmatik to control the engine or through the process modules I / O digital and analog.
Programmable Logic Controllers (PLC) is a computer that is easy to use electronic or user-friendly control functions that have for various types and levels of difficulty diverse. Definition Programmable Logic Controller is electronic systems that operate digital and designed for use in the environmental industry, which uses a memory system that can be programmed for storage in the internal instructions that implement specific functions such as logic, sequence, time, counter and operating aritmatik to control the engine or through the process modules I / O digital and analog.Based on the concept of PLC name is as follows:
Programmable
Show ability in terms of memory to store programs that have been made that easily changed the function or usefulness.
Logic
Shows the ability to process the input in the aritmatik and Logic (ALU), which is conducting operations compare, enumerate, multiply, divide, reduce, inverter, AND, OR, and others.
Controllers
Shows the ability to control and manage processes that produce the desired output
PLC is designed to replace a series of relay sequensial in a control system. In addition can be programmed, the tool can also be managed and operated by people who do not have the knowledge in the field of operation of the computer specifically. PLC has a programming language that is easily understood and can be operated when the program was created by using the software in accordance with the type of PLC used is entered.
This instrument works based on inputs that are depending on the circumstances and at a certain time then that will or ON-OFF-I output-output. '1' shows that the situation is expected to be met while the '0' situation is not expected to be met. PLC can also be applied to the control system that has a lot of output.
Labels: PLC
Posted by
openews
at
7:34 AM
0
comments
![]()
PLC Functions Tweet
PLC function and usefulness in practice PLC can be divided in general and specifically. PLC functions are as follows:
Control sequence
PLC to process the input signal into a binary output that is used for the purpose of processing techniques sequentially, in order to maintain the PLC step in the right sequence of the process.
Monitoring Plant
PLC continually monitors the status of a system (such as temperature, pressure, high altitude) and take the necessary action in connection with a controlled process (for example, the value has exceeded the limit) or display a message on the service.
B. Special functions
PLC to provide input to the CNC (Computerized Numerical Control). Some PLC can provide input to the CNC to the interests of further processing. CNC when compared with the PLC has a higher accuracy and more expensive. CNC is usually used for the finishing process, establish working object, technology molding and so forth.
 The working principles of a PLC is to receive input signals a process manageable, then do a series of instructions to the logic input signals in accordance with a program stored in memory and generate output signals to control the Actuator or other equipment.
The working principles of a PLC is to receive input signals a process manageable, then do a series of instructions to the logic input signals in accordance with a program stored in memory and generate output signals to control the Actuator or other equipment.
Labels: PLC
Posted by
openews
at
7:16 AM
0
comments
![]()
Voice Over Internet Protocol Tweet
 Voice over Internet Protocol (VoIP), or with other Internet names Telephony is associated with the transmission of voice, is a technology for transmission of data including the usual form of data, voice or video in real time through the Internet (IP channel). In the transmission of voice applications, VoIP is strong candidate to replace the conventional phone network using the PBX (private branch exchange). This is because the cost is cheaper, especially for long-distance connection. Moreover, now said that the quality of the VoIP service can exceed the quality of network services conventional. In the process adoption, various obstacles appear, especially for telecommunications technology company in such a way so that difficult to 'upgrade ' networks.
Voice over Internet Protocol (VoIP), or with other Internet names Telephony is associated with the transmission of voice, is a technology for transmission of data including the usual form of data, voice or video in real time through the Internet (IP channel). In the transmission of voice applications, VoIP is strong candidate to replace the conventional phone network using the PBX (private branch exchange). This is because the cost is cheaper, especially for long-distance connection. Moreover, now said that the quality of the VoIP service can exceed the quality of network services conventional. In the process adoption, various obstacles appear, especially for telecommunications technology company in such a way so that difficult to 'upgrade ' networks.
Labels: VoIP
Posted by
openews
at
5:55 AM
0
comments
![]()
VoIP Interfaces Tweet
Design and development goal is to enable H.323 interoperability with other types of multimedia terminals. With a standard terminal H.323 can communicate with H.320 terminals on the N-ISDN, H.321 terminals on the ATM, and H.324 terminal switched on the Public Telephone Network (PSTN). Terminal H.323 real-time communication allows two-way form of voice, video and data. H.323 standard consists of 4 components of physical I used when connecting communication multimedia point-to-point and point-to-multipoint on some kind of network:
 Terminal
Terminalmultimedia communications for the real-time two-way. Terminal H.323 can be a personal computer (PC) or other means of self that can run multimedia applications.
Gateway
Used to connect two different networks, namely between H.323 network and a network of non H.323, for example, the gateway can connect and provide communication between the terminals with H.233 phone network, for example: PSTN. In the form of a network connecting the two different done with the protocols for call setup and release and send information between networks connected to the gateway. However gateway is not needed for communication between the two terminals of H.323.
Gatekeeper
Can be considered as a brain on the network because H.323 is a point important in the H.323 network.
MCU
Used to service the terminal H.323 conference three or more. All terminal who want to participate in the conference can build relationships MCU with the materials for the conference, negotiations between terminals to ensure the audio or video coder / decoder (codec). According to the H.32 standard, a MCU consists of a Multipoint Controller (MC) and several Multipoint Processor (MP). MC Negotiations handle H.245 (concerning signaling) between the terminals to determine the ability audio and video processing. MC also to control and determine the series audio and video will be multicast. MC does not face directly the media. This task was given to the MPs who make Mix, switches, and process audio, video, or bits - bits of data. Gatekeeper, gateway, MCU and the logic is a separate component in the standard H.323 but it can be implemented as a means of a physical.
Labels: VoIP
Posted by
openews
at
5:30 AM
0
comments
![]()
How To Access The VoIP Tweet
 To access the necessary VoIP Terminal Adapter or SoftPhone. SoftPhone is a software-based VoIP terminals such as Netmeeting. For it is necessary Soundcard computer equipped with a headphone and microphone following. Connection to The Internet can use a dial-up modem or xDSL. theoretically modem 14.4 kbps is sufficient for the learner-VoIP.
To access the necessary VoIP Terminal Adapter or SoftPhone. SoftPhone is a software-based VoIP terminals such as Netmeeting. For it is necessary Soundcard computer equipped with a headphone and microphone following. Connection to The Internet can use a dial-up modem or xDSL. theoretically modem 14.4 kbps is sufficient for the learner-VoIP.However, DSL Flatrate better for VoIP. Neither because the higher the speed, but the connections of 24 hours. So that VoIP normal telephone functions such as: contact and can be contacted at any time. To This actually needs more appropriate when used TA (Terminal Adapter).
TA is a from of the small aircraft that can be connected to a VoIP network without using the computer. So the computer does not have to light only for 24 hours standby waiting for incoming phone calls. In addition to electricity also noisy. You can connecting ordinary telephones (including wireless telephones) to the TA, so that you there is no need to use headphones or a microphone. With VoIP TA really feels like a normal telephone.
Labels: VoIP
Posted by
openews
at
5:25 AM
0
comments
![]()
Offshore Communication With WiMAX Tweet
Sunday, November 16, 2008

Cable solutions are not appropriate for this scenario, because the facilities offshore, and since oilrigs are moved regularly and are in the field of oil or gas. Communication to monitor the status of the assets can be maintained, using battery-supported WiMAX terminals. Communication with WiMAX networks have a large bandwidth and multiple modulation used in accordance with the distance including BPSK,QPSK,16-QAM and 64-QAM. When equipped with a high-power amplifier and operating with a low-level modulation namely BPSK or QPSK.
Labels: WiMAX
Posted by
openews
at
5:57 AM
0
comments
![]()
Optimization WAN Tweet
Saturday, November 15, 2008
The performance of low priority because the applications to compete with the critical resources for WAN applications. In addition, the lack of manageability occurred because of how the application and make a WAN can not be seen. Key from the WAN Optimization is the compression and caching, acceleration, application visibility and control. Each region cut costs and increase productivity.
They also improve access to share resources, enhance recovery, enable the roll-out new applications, reducing the time to problem-shoot, much the spread of automation devices and, ultimately, manage the site without local staff. In addition to this, users improve productivity, save money applications such as VoIP enabled applications and can get a critical priority.
Compression and caching sequence needs to be done because the organization running the application with the traffic of different characteristics, needs a combination of a decrease in IT equipment to improve WAN caching capacity. In order operate on shared data in the file structure of the web page, so that they can even eliminate repetition in the modified files.
If a WAN pipe is not full, but users continue to complain about the performance of applications, the opportunity that latency is a mistake. Latency can affect the application layer on a different sometimes it's the behavior of the TCP slow applications, such as FTP and transfer applications, and sometimes the application Layer protocol. Accelerating TCP will do anything to expedite the application because they send data in small and even smaller than the TCP how, so that the open TCP window size does not help them until they are accelerated in Layer 7.
Then, TCP acceleration can also kick in to expedite the application. WAN optimization and acceleration technology designed to improve the performance of applications and to improve the user experience without having to increase bandwidth or reduce latency.
Labels: Computer
Posted by
openews
at
6:18 AM
0
comments
![]()
Online Fraud Protection Tweet
Tuesday, November 11, 2008
In the last six months of 2007, Symantec observed more than 85,000 phishing hosts. Fraud attacks become more sophisticated and increasingly targeting business customers and devastating. Organization generally less effective to overcome online fraud. Symantec's Global Intelligence Network also Provide a comprehensive view of Internet attacks. Security intelligence activities is based on data collected from in the world. Symantec's Global Intelligence Network that analyzes data from more than 2 million email accounts, 120 million system and over 40,000 devices in more than 200 countries.
Online fraud protection include:
Phishing monitoring:
Phishing attacks on the client's brand. Transaction monitoring: Review on the back-end transaction systems and blocks fraudulent activities.
Online Fraud countermeasures:
To respond quickly to the attack to minimize losses and protect the reputation of the brand
working with ISPs to reduce the activities of fraudsters.
Malware Intelligence and Analysis:
Provides monitoring of malware targeting specific and the brand new malware analysis behavior.
Education and Consumer Protection:
Help organizations educate and protect their customers from online enduser
threats and minimize risk fraud.
From the above data should protect ourselves from online fraud to minimize the losses that will occur. Many antivirus software that can protect you, so do not wait, especially before they occur.
Labels: Antivirus
Posted by
openews
at
9:48 AM
0
comments
![]()
Routing Data Packet Using Tracert Tweet
Monday, November 10, 2008
This below example result routing from my computer:
traceroute to yahoo.com (68.180.206.184), 30 hops max,
40 byte packets
1 vlan250.lon-service6.Melbourne.telstra.net (203.50.2.177)
0.264 ms 0.267 ms 0.294 ms
2 TenGigabitEthernet0-12-0-2.exi-core1.Melbourne.telstra.net
(203.50.80.1) 0.604 ms 0.436 ms 0.411 ms
3 Bundle-POS1.chw-core2.Sydney.telstra.net (203.50.6.13)
14.732 ms 14.772 ms 14.777 ms
4 Bundle-Ether1.oxf-gw2.Sydney.telstra.net (203.50.6.90)
14.897 ms 14.926 ms 14.931 ms
5 TenGigabitEthernetx-0.syd-core04.Sydney.reach.com
(203.50.13.18) 15.287 ms 15.238 ms 15.362 ms
6 static.net.reach.com (202.84.140.229) 162.323 ms
162.181 ms 162.201 ms
7 static.net.reach.com (202.84.251.74) 162.324 ms
162.535 ms 162.361 ms
8 yahoo.paix05.net.reach.com (134.159.63.22) 195.028 ms
194.956 ms 194.941 ms
9 ae0-p141.msr1.sp1.yahoo.com (216.115.107.51) 195.051 ms
ae1-p151.msr2.sp1.yahoo.com (216.115.107.79) 195.011 ms
ae0-p141.msr1.sp1.yahoo.com (216.115.107.51) 195.075 ms
10 te-9-1.bas-a1.sp1.yahoo.com (209.131.32.21) 195.217
ms te-8-1.bas-a1.sp1.yahoo.com (209.131.32.17) 195.377
ms te-9-1.bas-a1.sp1.yahoo.com (209.131.32.21) 195.211 ms
11 * * *
You can using instructions: C> tracert domain ->
example tracert my blog C>tracert adrianindo.blogspot.com
or using here
Labels: Computer
Posted by
openews
at
12:32 PM
0
comments
![]()
International Paid Surveys Tweet
Can follow the money with the survey program. MindField Online is the solution to get additional cash income. You can work from home, office or anywhere you have access to the Internet. You need to do is participate in a variety of interesting opinions from the research survey. You get cash for each survey you complete. Dare to try to please sign up
SurveySavvy™ online community
This online survey that will provide incentives of 20% of the online community. Incentives are given when you're finished with the survey complete. This online survey will provide an additional incentives when you refer to your friends or your family. If you are interested try here
Labels: Affiliate , Making Money , Paid Surveys
Posted by
openews
at
9:32 AM
0
comments
![]()
Increase Your Traffic With Buy Blog Tweet
Sunday, November 9, 2008
You choose to live blog or website that complies with the requirements of existing prepare. Terms of which you can select is the ranking of blogs and the budget offered. To buy a blog for the review of the product or increase the traffic, please visit here
Labels: Affiliate , Making Money , Web Traffic
Posted by
openews
at
8:40 AM
0
comments
![]()
PPC And Post Program Tweet
PPC program will pay you to do when visitors click on ads that are displayed and a link will appear automatically on the content of each post if you accordance with the keyword ads. To follow this program please visit here
Labels: Affiliate , Making Money
Posted by
openews
at
8:23 AM
0
comments
![]()
Making Money With Your POST Tweet
To follow the program paid per post this, your blog must meet the requirements specified by the owner of the program review. Money obtained in accordance with the many visitors who come to your blog. Traffic your blog is very important because this is an important requirement in the program this. For to try this program, please visit to Buy Reviews
Labels: Affiliate , Making Money
Posted by
openews
at
7:39 AM
0
comments
![]()
Money From Selling Products Tweet
Friday, November 7, 2008
The more products that we sell so many more of the money given by the owner of the product. When we have become a part of this affiliate program, then we will get the tools that are used to selling products, such as the duplication of the website, content, links, banners.
Example link http://www.example.com/?id=19504, id= 19504 is a seller ID. Affiliate programs continue to progress without any time limit or a lifetime for owners of the products continue to sell products. With this affiliate program we will get a monthly salary when the product sold. Many of the money given to 30% of the price of products sold. To try the program afialiasi please click banner for sign up.
Labels: Affiliate , Making Money
Posted by
openews
at
9:02 AM
0
comments
![]()
Internet Marketing Tweet
Monday, November 3, 2008
Delivery of this email must follow the rules applicable law or the rules that exist, which is aimed at sending someone to do. Delivery of the email that is not the objective will be considered in spamming is prohibited and that is criminal.
So to use email marketing should be done with caution if we are not the domain or email our operations will be terminated by the owner of the service and consequently we can not use email or domain that.
Marketing using the website to make the marketing website, where the website is designed in such a way that reflects the contents of goals will be achieved. Examples of websites that have the money category, the website will contain the content matters related to money.
Similarly, the website has a category of techniques, the site content is the main issues related to technical problems. Marketing with the discussion forums that discuss specific topics, such as cooking forum, forum marketing etc. By using this forum for discussion, target marketing can be achieved if the marketing is done in accordance with the discussion forum.
Labels: Marketing
Posted by
openews
at
4:02 AM
0
comments
![]()
Highly Eliptical orbit (HEO) Tweet
Monday, October 13, 2008
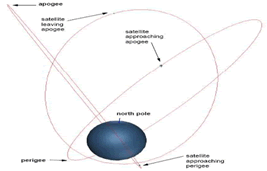
Labels: Satellite
Posted by
openews
at
11:47 AM
0
comments
![]()



